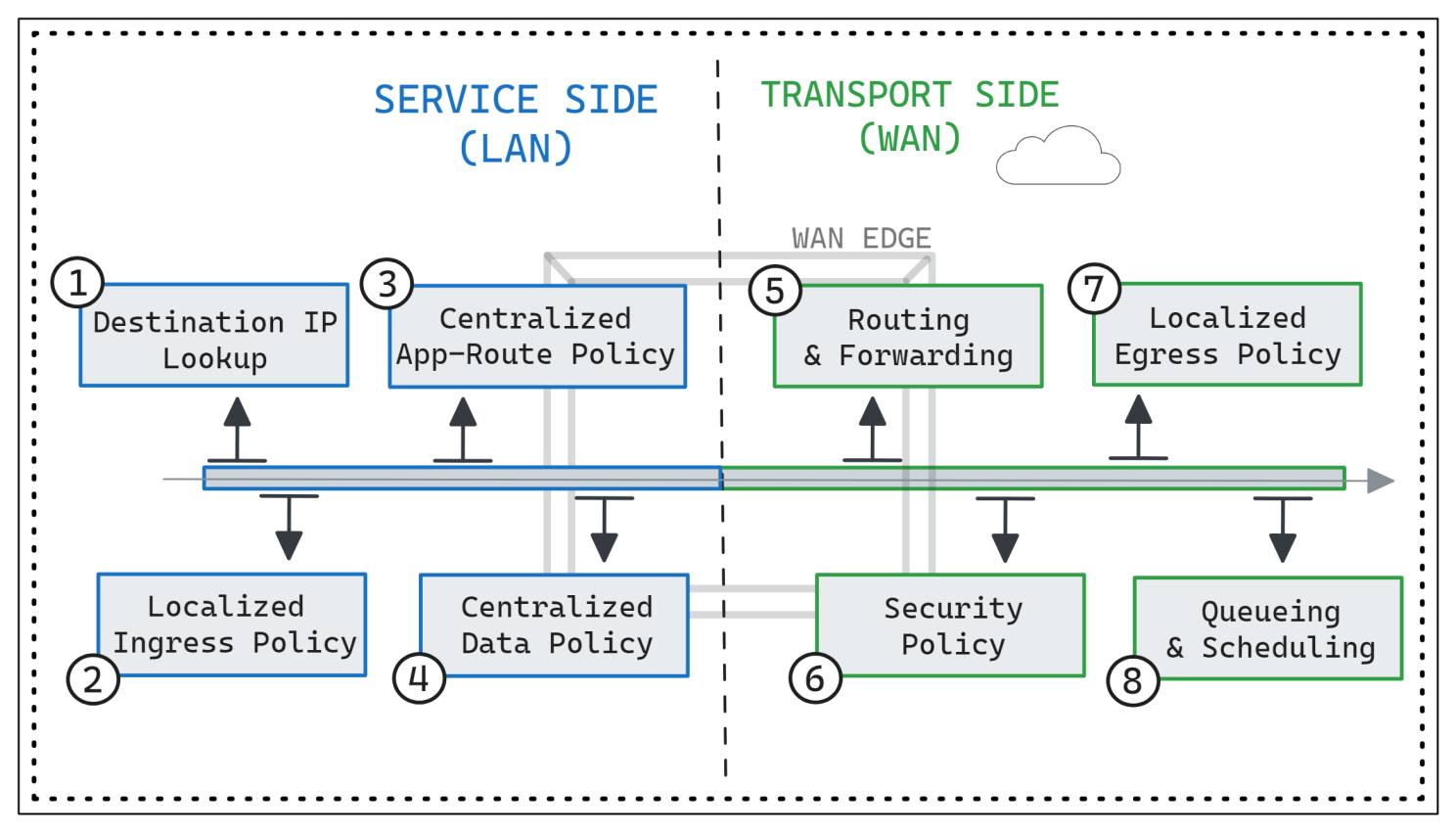
About the packet forwarding order of operations, given that various policies can influence the forwarding of a single flow at a site, it's crucial to comprehend how these policies are applied, evaluated, and interacted.
Firstly, control policies operate separately from data plane policies as they don't directly affect data plane operations. Instead, they influence the routing information upon which the data plane relies, thereby impacting traffic forwarding.
Control policies can modify, filter, summarize, or restrict the advertisement of routing prefixes or TLOCs. Consequently, a WAN Edge device will construct its forwarding plane based on the altered control plane information.
Figure 1-1. Cisco WAN Edge Packet Forwarding Order of Operation
When a packet traverses a WAN Edge router, it follows a carefully orchestrated sequence of steps:
IP Destination Lookup: The router begins by examining the destination IP address of the packet. It consults its routing table to determine the most appropriate next-hop for forwarding the packet. This lookup is crucial as it guides all subsequent forwarding decisions.
Ingress Interface ACL: Next, the packet encounters any ACLs configured on the ingress interface. These ACLs, often part of localized policies, dictate whether the packet should be allowed, denied, or subjected to specific actions like traffic shaping or Quality of Service (QoS) markings. If the packet is denied by the ACL, it is dropped immediately and not processed further.
Application-Aware Routing: Following the routing decision based on the routing table, the packet undergoes evaluation against an Application-Aware Routing policy. This policy is designed to optimize traffic based on application-specific requirements. However, it's important to note that Application-Aware Routing can only differentiate between paths of equal cost in the routing table. If multiple next-hop addresses for a destination don't have equal-cost paths, the Application-Aware Routing policy has no impact, and the packet follows the most preferred path based solely on the routing table.
Centralized Data Policy: Once Application-Aware Routing is applied, the packet's journey may be further influenced by centralized data policies. These policies have the authority to override decisions made by Application-Aware Routing, providing additional control over traffic forwarding.
Routing and Forwarding: With the routing decisions made, the router determines the appropriate output interfaces for the packet's continued journey.
Security Policy: If configured, the packet is subjected to various security measures in a predefined order. These may include firewall rules, intrusion prevention systems (IPS), URL filtering, and advanced malware protection. Each security measure is applied according to its configured rules and policies.
Encapsulation and Encryption: As the packet prepares to traverse the fabric, it undergoes encapsulation and encryption processes to ensure secure transmission across the network. This includes adding VPN labels and applying tunnel encapsulation as necessary.
Egress Interface ACL: Finally, the packet encounters any ACLs configured on the egress interface before leaving the router. Similar to the ingress ACLs, these ACLs may permit, deny, or manipulate the packet's contents based on predefined rules. Any modifications or denials applied here take effect before the packet is forwarded out of the router toward its final destination.
How Cisco SD-WAN Data Plane works?

![[Cisco SD-WAN] WAN Edge Packet Forwarding Order of Operations](https://cdn.hashnode.com/res/hashnode/image/upload/v1710383702910/285d116a-c00a-4ada-8d46-5e9593c875e5.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)